The use of intrusion detection/prevention systems is good practice in any company: they prevent cyberattacks, monitor network traffic, and issue alerts for potentially suspicious activities; These “signals” are generally sent to the event management system, SIEM (Security and Correlation Event Management). Most SIEM systems include an IDS (Intrusion Detection System), which avoids installing and configuring different solutions: the first configuration is very important due to false positives and having one solution can be an asset. Of course, it will depend from case to case, and therefore, the choice you make must be adapted to the needs of each person.
How do you choose the best solution?
The two most common types of intrusion detection systems are HIDS (Host-Based Intrusion Detection System) and NIDS (Network Intrusion Detection System). HIDS only monitors packets entering and leaving each device, compares files to identify any changes (or deletions) and sends an alert accordingly; However, it requires a proxy installed on each device.
On the other hand, NIDS scans the traffic passing through the network, which helps to identify potential attacks or “abnormal” behavior. Using both allows for more complete analysis, detection and prevention, but the hardware requirements of a HIDS solution are smaller and easier to configure – there are many open source solutions for this, with their own advantages and disadvantages.
Creating such a system at home will not be useful for most users. However, if you have servers and many computers and services communicating with the outside, it might be interesting to consider an intrusion detection and event management solution.
meerkat and your zik
These are two common solutions if you are looking for NIDS. Suricata is a more complete alternative to the well-known Snort, since it also collects data from the application layer; Monitors activity on TCP, UDP, IP, ICMP and TLS protocols; Scans real-time traffic from network applications such as SMB, FTP, and HTTP; Integrates with other tools such as Squil and Snorby; It uses hardware acceleration architecture, uses different processors, and can even work partially on the graphics card.
Zeek, in addition to being an intrusion prevention system, is a traffic analyzer that facilitates the sorting of aggregated metadata and the production and segmentation of high-quality logs. Since Suricata is more efficient at monitoring traffic for known threats and producing alerts when they are detected, there can be an advantage to using both.
Onion safety and weight
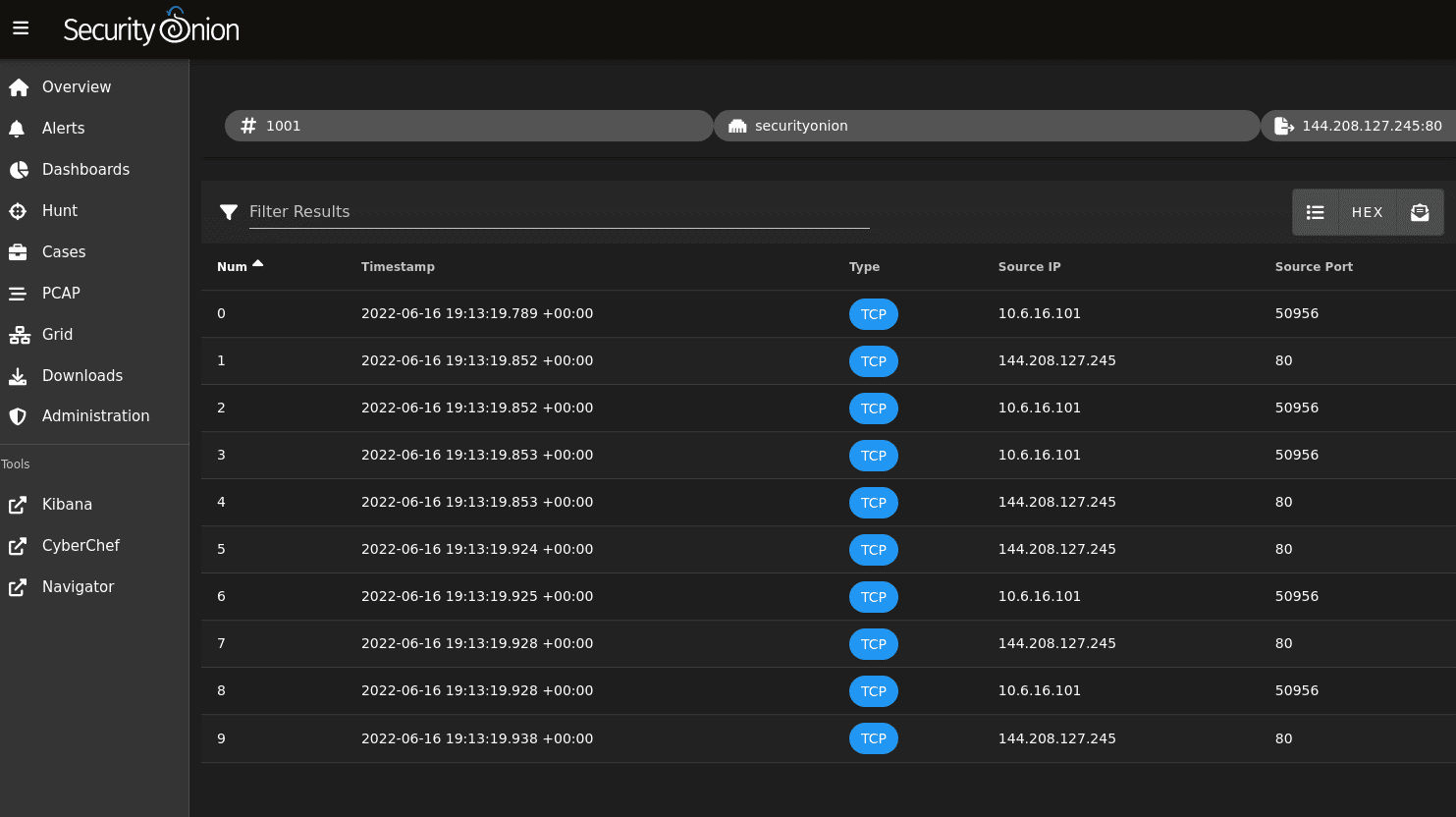
Security Onion is basically a Linux distro based on Ubuntu and has many tools installed: Wazuh such as HIDS, ELK (Elastic search, Logstash, Kibana), Suricata, Zeek, Stenographer, Cyberchef, Networkminer, among others. If you are looking for a complete solution, this is an option to consider; The downside is that it requires more hardware resources.
Wazuh is HIDS based on OSSEC (Open Source Host Based Intrusion Detection System) and offers more ease of installation/configuration, due to the good documentation it provides.
Kismet
If prevention is important for a wired network, it is even more important for a wireless network. For this purpose, an interesting solution is Kismet. This solution monitors wireless networks, including Wi-Fi and Bluetooth: if you have RF-based mice and keyboards, or a smart home with Zigbee sensors, they will be detected. To capture packets from a Wi-Fi network, it is necessary to put the system in “monitor mode” or “rfmon”, which allows data to be passed to the operating system. Kismet can be installed on dedicated hardware such as the Raspberry Pi or Hak 5 Wi-Fi, and can be accessed through the graphical web interface on port 2501. Since it is not the most user-friendly software on the market and requires good configuration to get the desired results, our suggestion is that you see the documentation on The official website, which explains how to do everything.
USIC
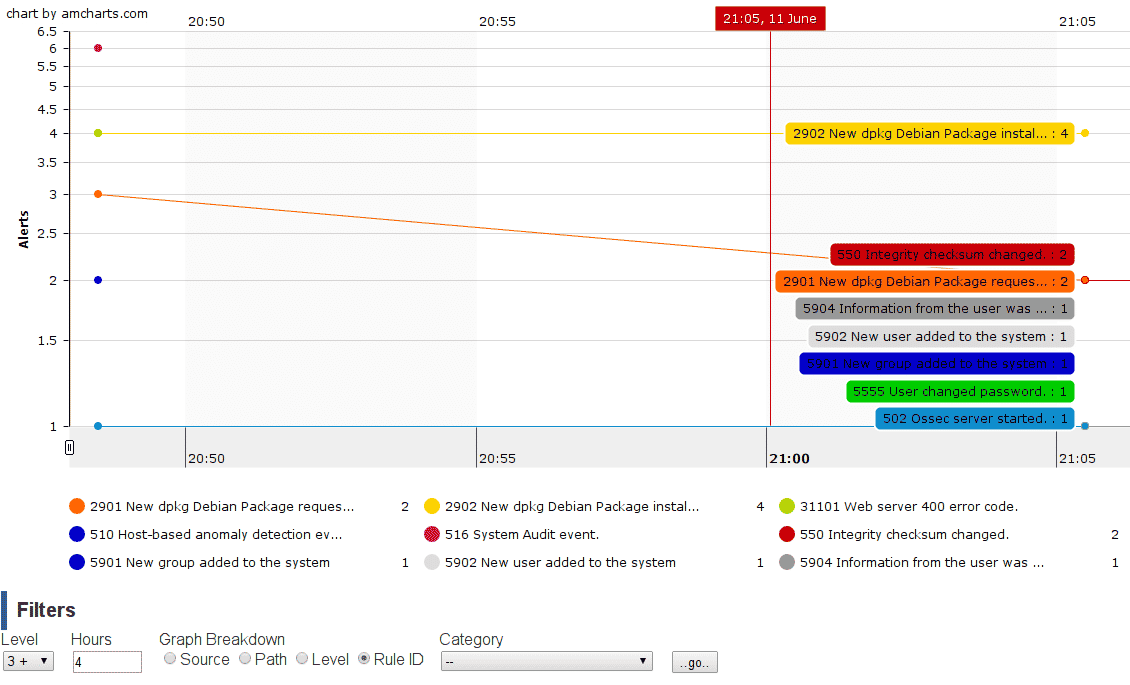
Ossec is a well known HIDS used in business environments, as it has been in the market since 2008 and for the trust it has given to those who use the tool. It identifies possible suspicious changes to system files, detects rootkits and malware, among other threats. The architecture is a client server and thus can run with or without a proxy; Logs can also be collected from a system log, for example.
Compared to Wazuh, the installation and configuration is not so simple and the simplest open source version has some limitations, such as the lack of an ELK package that Wazuh already includes. This facilitates centralization and visualization of logs, but the installation ends up being lighter, as well as allowing for gradual integration of other defense tools.
conclusion
There are other solutions and more details, not only about each of the tools, but also about the operation of various IDS systems. More than the choice of the tool, it is its composition that matters, because it takes time to clean up the false positives that appear. At home, I use Wazuh and the next goal is to install Suricata and Zeek, centralizing records in Wazuh.
To use NIDS, it is recommended that you have at least two NICs – so it is generally easier to start with HIDS. I have already tested Security Onion 2, but it requires more hardware resources, despite the ease of installation.
For a simple and accurate traffic analysis, you can use the TCPDump program, which analyzes the traffic and sends it to a file; Then use Zeek to read it and break the information down into simpler files.

“Coffee trailblazer. Social media ninja. Unapologetic web guru. Friendly music fan. Alcohol fanatic.”